When the authorities say cash leads to tax evasion, counterfeiting, etc., the common man (“Joe”) thinks it’s because cash is anonymous. When they goad him to ditch cash and move to digital payments, Joe assumes that digital payment will eliminate fraud because it’s not anonymous.
Then, one day, Joe uses a digital payment like UPI to buy something from, say, “Jane”. When he does not get what he ordered, he instinctively feels defrauded.
Man Flattered Spam Caller Believes He Has Car, House, Savings Account To Defraud https://t.co/xfDxNfciQu pic.twitter.com/KxFOknZ5Jg
— The Onion (@TheOnion) April 23, 2022
Joe contacts his bank (“Payor Bank”) and supplies the details of the payment including the mobile phone number of Jane, the Alleged Scammer. From the UPI ID, it is possible to infer the details of the bank to which Joe’s money went – this is the bank in which Jane has her account (“Payee Bank”).
Contrary to Joe’s expectations, his bank will not be able to retrieve the money from the Payee Bank.
That’s because, as an Account-to-Account Real Time Payment (A2A RTP), UPI is designed to be an irrevocable Method of Payment (MOP). In plain English, “Irrevocable” means “once gone, gone forever”. The same is true for all other A2A RTPs like FPS (UK) and Zelle (USA). Therefore, the Payor Bank will throw up its hands and tell Joe to file a police complaint.
Joe then goes to the cops and expects them to nab the Alleged Scammer immediately because he can supply her mobile number and / or UPI ID (aka Personally Identifiable Information). Instead he finds it hard to even get the cops to register his complaint.
In a normal burglary, there’s usually a tampered lock, broken glass or some anomaly. The victim can use that as evidence to file a complaint with law enforcement. However, in the case of a cybercrime, there’s no ostensible evidence of crime. It comes down to the Scammee’s word. While the Scammee can show the debit entry for the money exiting his bank account, that’s not proof that the Alleged Scammer has received the money. This is because, unlike credit card, A2A MOPs do not provide a legally-valid receipt (with the sole exception of FPS UK that I know of). See PSA: Insist On Receipt When You Pay By NEFT, UPI, FPS Etc. for more details.
Let’s say he crosses that hurdle and persuades law enforcement to investigate the theft. The cops will need to find out the address of Jane, the Alleged Scammer, and nab her. The Scheme Operator – National Payments Corporation of India (NPCI) in the case of UPI – might seem the logical place to start the search but scheme operators generally fob off fishing expeditions by cops (as they should, if you ask me).
I doubt if that's the case but taking it at face value, kudos to the powerful for upholding their fiduciary duty of not giving away their internal info in response to fishing expeditions by others.
— Ketharaman Swaminathan (@s_ketharaman) November 27, 2021
So law enforcement will need to approach the Payee Bank with the mobile number of the Alleged Scammer.
The Payee Bank has done KYC before opening Jane’s account. Therefore, it knows the identity, mobile number and address of Jane. However, due to banking secrecy laws, the Payee Bank can’t reveal its customer details just like that. It will insist on a court order.
 After law enforcement comes back with a subpoena, the Payee Bank will release Jane’s contact information and cops can go and nab her.
After law enforcement comes back with a subpoena, the Payee Bank will release Jane’s contact information and cops can go and nab her.
But, by that time, Jane could have decamped with the money. Remember that we’re talking about a real time payment method like UPI or FPS or Zelle, where Jane gets the money in her bank account a few seconds after Joe has sent the money out from his bank account, whereas the other activities will take a couple of days (or more if the cybercrime crosses state borders, leading to jurisdiction issues prolonging matters).
PSA: Whether it's heart attack, stroke or payment fraud, Golden Hour is critical. TAKE IMMEDIATE ACTION!!! pic.twitter.com/7HlpHq8z2o
— Ketharaman Swaminathan (@s_ketharaman) November 2, 2021
The Payor Bank can’t do anything. The Payee Bank won’t do anything. Cops can’t do much.
That’s why it’s hard to catch cybercriminals.
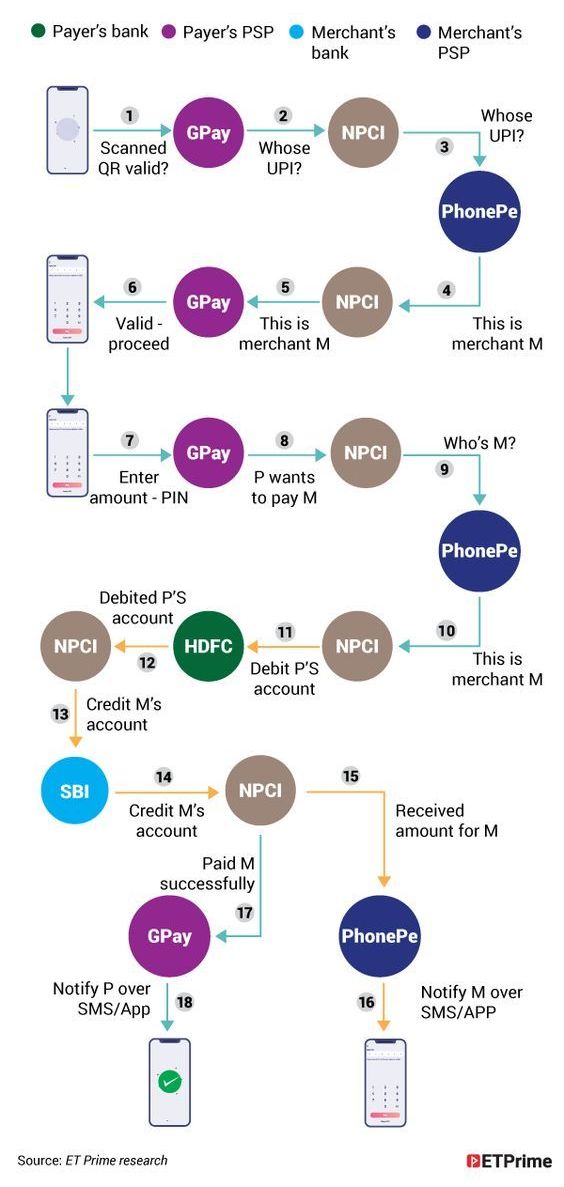
PS: As shown in the following exhibit, UPI / A2A Payments involve Payment Gateways, Payment Service Providers, and many more parties. They make matters even more complicated than explained above. But I’ve ignored them in the interest of describing the crux of the cybercrime problem in as simple a manner as possible.
Quora Link: https://qr.ae/pG3YDo